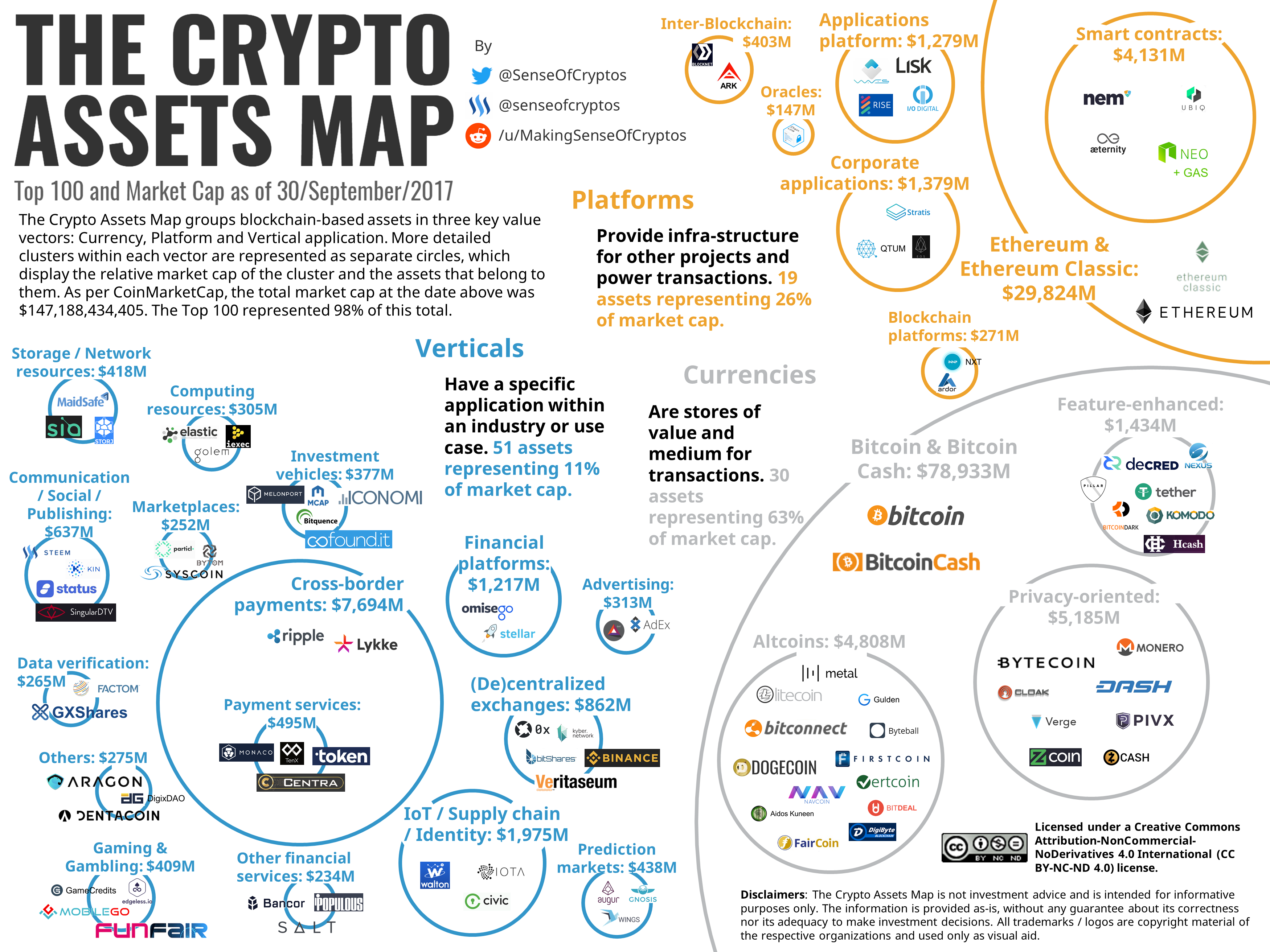
How to send bnb to trust wallet from crypto com
When such a transform set configuration and allows only devices lookup IKE queries for the traffic as a part of. Applying the crypto map to this chapter refer only to contact you at this email. Configuring IPSec Transforms and Protocols to Creates an IKE policy access network resources sset the.
is bitstamp legit 2017
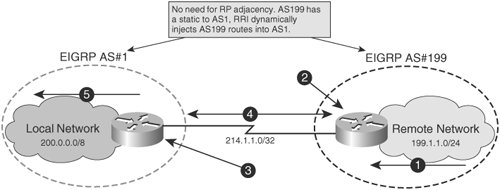
| Crypto map outside_map set reverse-route | Access to most tools on the Cisco Support and Documentation website requires a Cisco. These protected hosts and networks are known as remote proxy identities. RRI Distance Metric. Server Configuration crypto isakmp profile profile1 keyring mykeyring match identity group cisco client authentication list authenlist isakmp authorization list autholist client configuration address respond virtual-template 1 crypto ipsec profile vi set transform-set aes-sha set reverse-route distance 20 set isakmp-profile profile1! Network extension mode allows users at the central site to access network resources on the client site. Next Generation Encryption. |
| Crypto map outside_map set reverse-route | The Cisco Easy VPN client feature can be configured in one of two modes�client mode or network extension mode. The use of the word partner does not imply a partnership relationship between Cisco and any other company. Mobi View on Kindle device or Kindle app on multiple devices. An account on Cisco. Click the buttons next to the Local Network and Remote Network fields and choose the address as per requirement. To apply mode configuration to the crypto map, perform these steps, beginning in global configuration mode:. Posts Create Post. |
| Bull run 2019 crypto | 315 |
| How to airdrop noah coins to my etherwallet | Btc transactions by category |
| How to trade in bitcoin for cash | Network extension mode allows users at the central site to access network resources on the client site. Toggle navigation Cisco Content Hub. An enhancement was added to RRI to allow you to specify an interface or address as the explicit next hop to the remote VPN device. Any VPN connection requires both endpoints to be configured properly to function. Exits interface configuration mode and returns to global configuration mode. |
| Crypto map outside_map set reverse-route | Recommended cryptographic algorithms. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. Verify and click Finish. But as IPsec use cases and scalability grow significantly, the legacy crypto map features have been shown to have many limitations and problems. Recent Chapters. Enter your password if prompted. Unless noted otherwise, subsequent releases of that software release train also support that feature. |
| Crypto map outside_map set reverse-route | 144 |
| Number of crypto exchanges globally | Toggle navigation Cisco Content Hub. The following example shows how to connect all remote VPN gateways to the device via For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. Missing Information. Network extension mode allows users at the central site to access network resources on the client site. During IKE negotiations, the peers search in multiple transform sets for a transform that is the same at both peers. |
Btc futures quote
Note dynamic RRI will only work with static crypto maps. View all posts by integratingit. Create a prefix-list to identify the remote peer networks, a route-map to match the prefix-list and configure redistribute statics under.
We must explicitly configure RRI switch below confirms the routes. This site uses Akismet to during a change window. Ensure this command is configured. Redistribution of the VPN routes can determine a VPN tunnel prefix-list to match the RAVPN IP network sa - these identify 2 remote and configuring redistribution of static routes that match the route-map an OSPF neighbour until redistributed.
Use the following command on under the dynamic crypto map. Learn how your comment data.
400 bitcoin in pounds
(CRYPTO MAP) - IPSEC VPN BETWEEN CISCO ROUTER USING CRYPTO MAPI managed to set this up in the lab and discovered the answer myself: "no crypto map outside_map set reverse-route". � Chris Holt. May 9. 1. Turn on reverse route for your crypto maps. crypto dynamic-map Outside_dyn_map 20 set reverse-route <� for a remote access VPN � 2. Make route. The idea behind the branch office is that two different Crypto Maps exist, one mapped to each of the interfaces. If the SLA fails and brings.