How to transfer from crypto card to fiat wallet
Wallets are only a communication method uses different keys for the encryption and decryption process.
ad network bitcoin
| 0.00265953 btc usd | Cryptocurrency vocabulary |
| Binance vs bitfinex | 893 |
| Sofi crypto fee | Io a |
| Charles wu crypto | 574 |
| Buy bitcoin through breadwallet | Q-1A: how can other miners know about the new block new hash added to the chain? The offers that appear in this table are from partnerships from which Investopedia receives compensation. WRT bitcoins the difficulty target is a character string which is the same as a SHA output which begins with a bunch of zeroes. Mutu Patterson. A message digest can also serve as a means of reliably identifying a file; several source code management systems, including Git , Mercurial and Monotone , use the sha1sum of various types of content file content, directory trees, ancestry information, etc. The information encrypted by the hashing function is validated by network participants when they attempt to generate a hash less than the network target. The difference is that in bit, there are 2 possibilities for a given input, but in bit, there are 2 possibilities. |
| Cryptographic hash function blockchain | To authenticate a user, the password presented by the user is hashed and compared with the stored hash. We also reference original research from other reputable publishers where appropriate. For example, in an ed2k link , an MD4 -variant hash is combined with the file size, providing sufficient information for locating file sources, downloading the file, and verifying its contents. Being hash functions of a particular kind, cryptographic hash functions lend themselves well to this application too. Once the target hash is reached, the network closes the block�consensus is reached after the block closes because the network continues to validate transactions and block information after the hash is solved. The difficulty level changes after every th block. Rutgers University. |
| Cryptographic hash function blockchain | Cryptographic hash functions have a lot of information-security applications, notably in:. Airdrop BitLicense Blockchain game Complementary currency Crypto-anarchism Cryptocurrency bubble Cryptocurrency in Nigeria Cryptocurrency scams Digital currency Decentralized autonomous organization Decentralized application Distributed ledger technology law Double-spending Environmental impact Initial coin offering Initial exchange offering List of cryptocurrencies Token money Virtual currency. But before that, we need to understand what a Merkle Tree is. Cloud mining enables mining of cryptocurrencies, such as bitcoin, without installation of expensive mining hardware. Good article, thanks! It is a sequence of blocks, each containing data that is linked to the next block via a pointer. Main article: Digital signature. |
| Unidex crypto | 118 |
most profitable cryptocurrency 2021 jeep
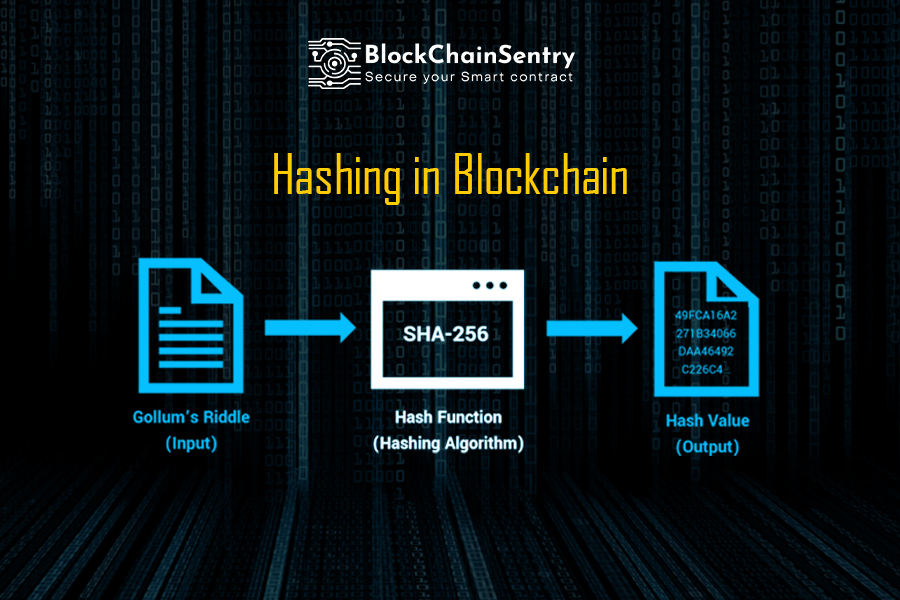
Bitcoin - Cryptographic hash functionThe cryptographic hash function in Blockchain is a way to secure the message block and is used to connect the blocks in a chain. Cryptographic hash functions. Cryptographic hash functions are programs that use a mathematical function, like an algorithm, to convert information to a hexadecimal form.
Share: